Active flaws in the PowerShell Gallery could be weaponized by threat actors to pull off supply chain attacks against the registry's users.
"These flaws make typosquatting attacks inevitable in this registry, while also making it extremely difficult for users to identify the true owner of a package," Aqua security researchers Mor Weinberger, Yakir Kadkoda, and Ilay Goldman said in a report shared with The Hacker News.
Maintained by Microsoft, PowerShell Gallery is a central repository for sharing and acquiring PowerShell code, including PowerShell modules, scripts, and Desired State Configuration (DSC) resources. The registry boasts 11,829 unique packages and 244,615 packages in total.
The issues identified by the cloud security firm have to do with the service's lax policy surrounding package names, lacking protections against typosquatting attacks, as a result enabling attackers to upload malicious PowerShell modules that appear genuine to unsuspecting users.
A second flaw pertains to the ability of a bad actor to spoof the metadata of a module -- including Author(s), Copyright, and Description fields -- to make it appear more legitimate, thereby deceiving unwitting users into installing them.
"The only way for users to determine the real author/owner is to open the 'Package Details' tab," the researchers said.
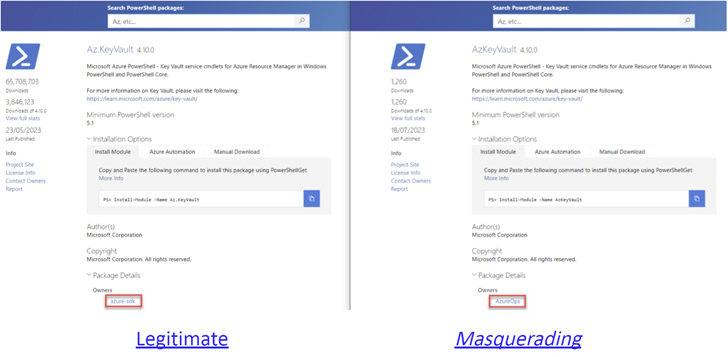
"However, this will only lead them to the profile of the fake author, as the attacker can freely choose any name when creating a user in the PowerShell Gallery. Therefore, determining the actual author of a PowerShell module in the PowerShell Gallery poses a challenging task."
Also discovered is a third flaw that could be abused by attackers to enumerate all package names and versions, including those that are unlisted and meant to be hidden from public view.
This can be accomplished by utilizing the PowerShell API "https://www.powershellgallery.com/api/v2/Packages?$skip=number," enabling an attacker to gain unrestricted access to the complete PowerShell package database, including associated versions.
"This uncontrolled access provides malicious actors with the ability to search for potential sensitive information within unlisted packages. Consequently, any unlisted package that contains confidential data, becomes highly susceptible to compromise," the researchers explained.
Aqua said it reported the shortcomings to Microsoft in September 2022, following which the Windows maker is said to have put in place reactive fixes as of March 7, 2023. The problems, however, remain reproducible.
"As we increasingly depend on open-source projects and registries, the security risks associated with them become more prominent," the researchers concluded.
"The responsibility for securing users primarily lies with the platform. It's essential that PowerShell Gallery, and similar platforms, take necessary steps to enhance their security measures."
IT had the stupid grind culture well before it became a meme.