I might be mistaken, but isn’t using a mixer considered money laundering in the US?
They seemed pretty well hidden initially despite being purple and heavily contrasting. Wasn’t until I started editing that I noticed.
It’s one of my favourite buildings in Sydney but oh boy does it have issues. I swear they have the scaffolding/footpath cover active most of the time.
The markets were on at the time. :)
Should be much better now. I've re-exported all the images in slightly lower quality and it's drastically reduced the file sizes.
If you only care about having a static IPv6 address take a look at TunnelBroker by Hurricane Electric. They give you free /48 IPv6 blocks tunnelled through their network. Words of warning though: 1) some ISPs block using this service (prevent the tunnel from working), 2) in my experience I’ve seen high latency due to weird routing, 3) those IPs ending up on blocklists due to abuse and 4) the tunnel is unencrypted so traffic between you and Hurricane Electric is trivially intercepted, though if that was a problem in the first place then you wouldn’t be hosting from your home network anyway so this is mostly moot.
IP blocklisting is still very much a thing as well so you can expect any mail originating from a residential IP to be rejected due to their /24 or larger having previously sent spam, and that assumes you can send server-to-server mail (destination port 25/tcp) in the first place since many ISPs and server providers block traffic destined to that port by default to prevent users from getting their IP blocklists. My home ISP blocks outbound SNMP traffic (or at least did 10 years ago) presumably to also prevent abuse. That said, things like blocking inbound port 80/tcp and 443/tcp is purely a measure to prevent people running servers at home which I’m not a fan of.
Same is true for any tech thing. Sure, you can buy a perpetual licence for something but if you’re running it on anything but an isolated device then you will at minimum need security updates or the source code to fix it yourself. Same is true for things like console games where eventually the hardware will just die and it may become too expensive to replace it. Even emulation is case-by-case since some games use obscure calls which have no adequate emulation. Software doesn’t exist in isolation. For that, you have to revert to pen, paper and some analog tech.
Ah you’re right about the GDPR part in the article! My bad. Signing might be the best bet in that case since it avoids storage IF you were to try and implement this kind of system.
The idea of having them send an e-mail to an address containing their IP is clever, however you need to authenticate that the person who sent the e-mail is either somebody who queried your site, or somebody that got the address from somebody who queried your site or else you could just figure out how to generate that base64 yourself and impersonate somebody else’s IP address which could have catastrophic results if you then fed these IPs into something like a block list and suddenly you’ve blocked Microsoft/Office 365. To be fair, I doubt anybody is going to try and reverse engineer one person’s code to then figure out how to impersonate who sent spam, but if this became a widely distributed program you could just pull off Github then it would be more concerning.
A couple ways to solve this:
- Sign the information before encoding it in Base64 so you can verify it came from your site and wasn’t just spoofed. This has the upside of being stateless since you don’t need to keep a record of every e-mail you’ve generated but comes with the disadvantage of spending CPU time signing the text which could be exploited as a DDoS.
- Spit out a random e-mail address and record which e-mail address was given to each IP. Presumably you wouldn’t hold on to this list forever since IPs change owners frequently and so an IP that was malicious 1 month ago could be used by a completely different person now and so you can trim this list down once a month to avoid wasting disk space. You’d probably also want to keep some amount of these requests in memory (maybe 10Mb or so) to avoid ruining your IOPS.
All this said, I think your time is better spent with the using unique e-mail aliases as the author suggested but with 2 changes: 1) use aliases which are not guessable to prevent somebody from making it look like somebody else was hacked (e.g. me+googlecom@ gets compromised, but the spammer catches on and sends from me+microsoftcom@ instead to throw off the scent) and 2) don’t use me+chickenjockey@, use chickenjockey@ or else the spammer can just strip “+chickenjockey” from the address to get the real e-mail address.
Eh it depends. I’m fortunate enough to be in a good IP block so I don’t get my e-mails dropped purely on that. It’s been a good learning experience and I’ve leaned on my own server a number of times for troubleshooting at work since I can see the whole mail flow. The only problem I have is the free Outlook/Hotmail will not accept my e-mails. Everybody else seems fine. All that said, I don’t host anybody else’s e-mail so I haven’t had any spam come out of my IP, and I would never in a million years host e-mail for a customer.





















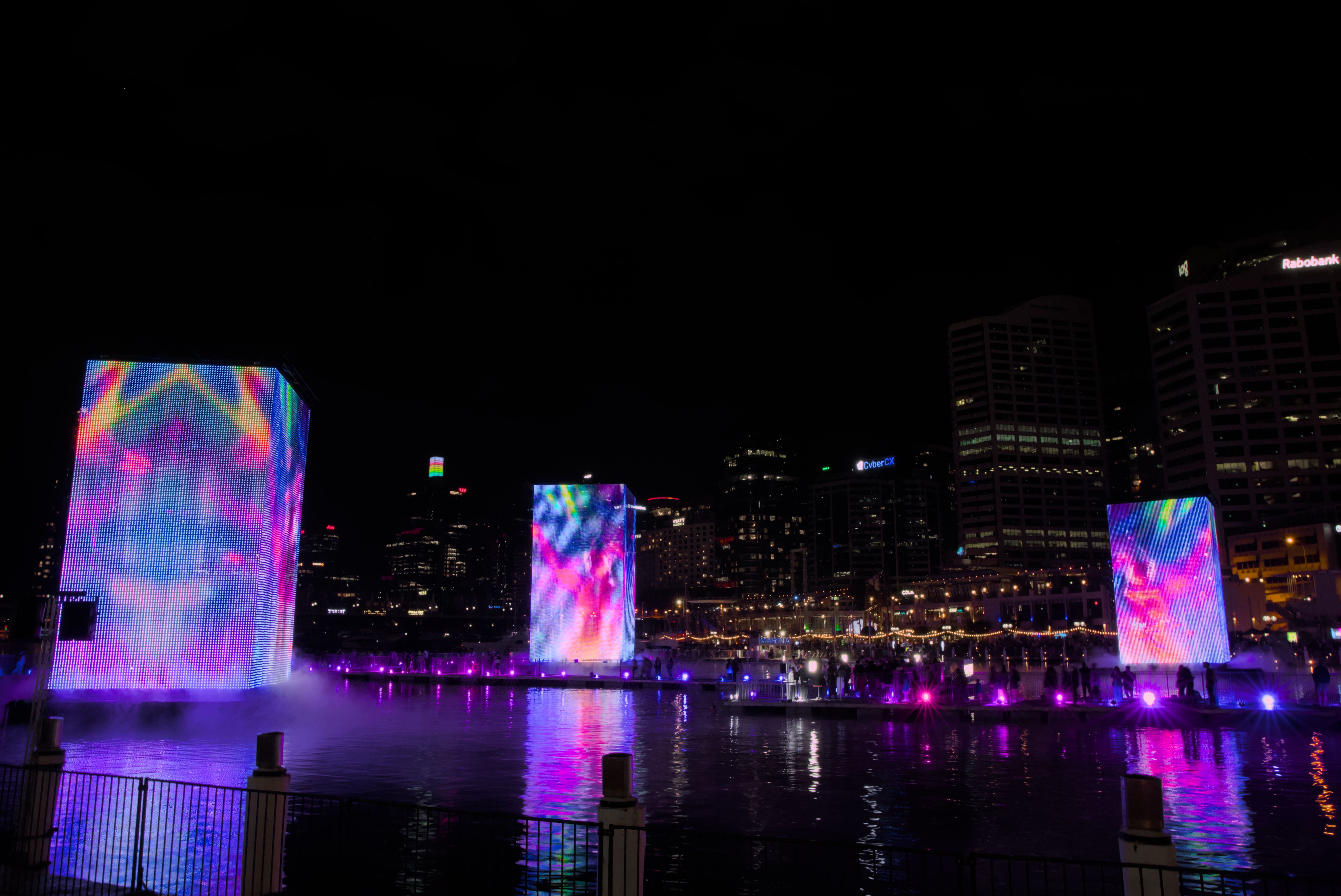























































































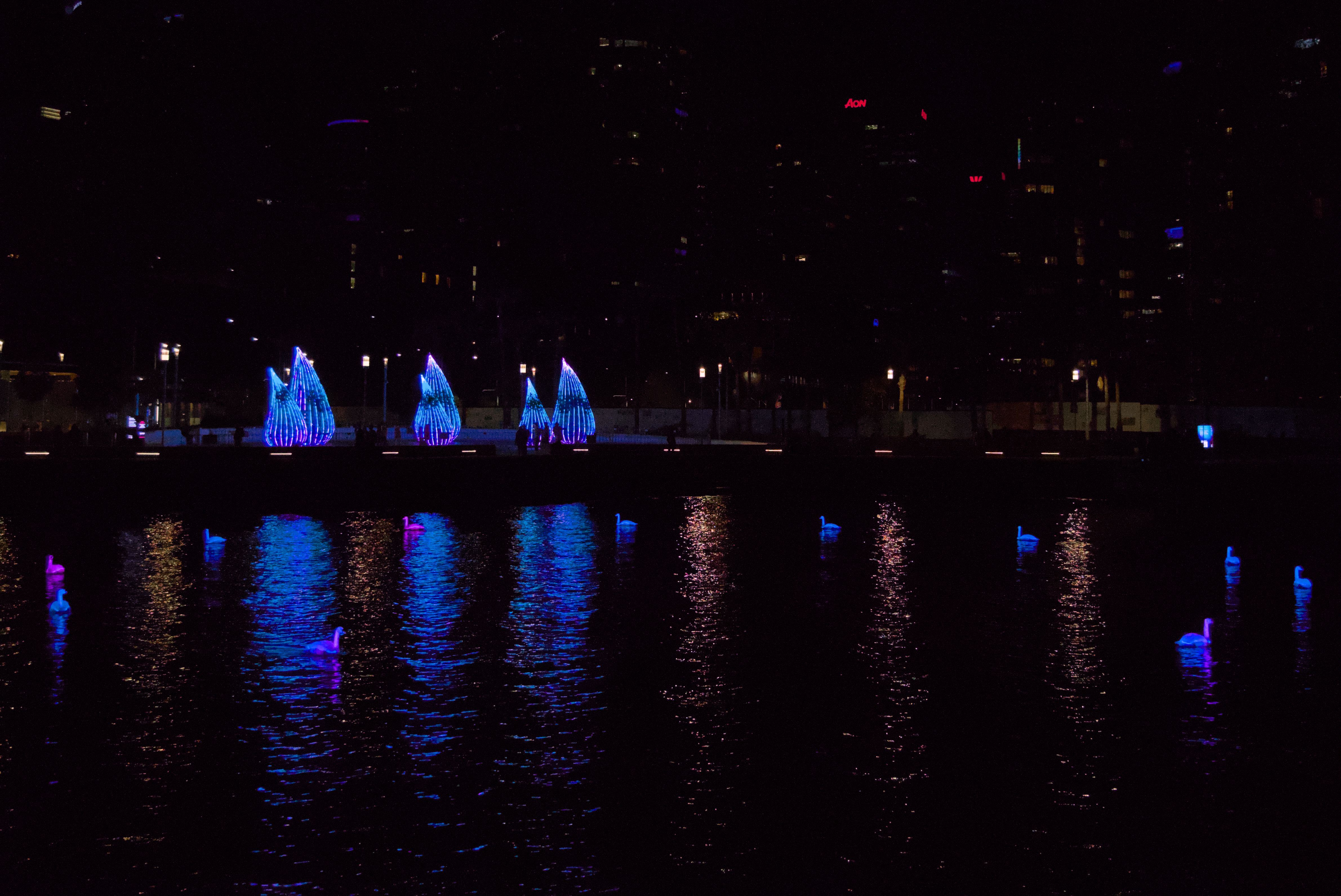









































This seems a bit convoluted as an explanation if I’ve understood it correctly. If Telegram as using a compromised hosting provider then you could have the strongest crypto in the world to prevent a man-in-the-middle from seeing the unique identifier for each device and it wouldn’t matter since they already who which user is which IP from the servers they control. They don’t stand to gain anything by exposing the unique string to MiTM attacks when they already control Telegram’s servers unless their goal is also to allow other countries to see which user has which IP too. It just seems like an incompetent implementation.